Overview
In this lab, I deployed and configured Microsoft Sysmon on a Windows Server 2022 virtual machine in Azure. The goal was to simulate attack behavior using PsPing and other network interaction tools and then analyze the logs generated by Sysmon. This simulates a workflow of monitoring system activity and investigating suspicious behavior.
This lab is part of a larger project to build a hands-on detection lab and document the process like a real-world SOC analyst.
Lab Setup
Cloud provider: Microsoft Azure
VM OS: Windows Server 2022
Tools:
- Sysmon v15.15
- Olaf Hartong’s modular Sysmon config
- PsPing v2.12
- PowerShell (Admin)
I provisioned the VM through the Azure portal and assigned it a public IP for RDP access.
Once the machine was up, I connected via Remote Desktop. A warning about the certificate not being trusted appeared, which is expected for self-signed certs.
Installing and Configuring Sysmon
First, I downloaded the Sysmon ZIP archive from Microsoft’s official source, extracted it, and launched PowerShell as administrator:
.\Sysmon64.exe -acceptEula -iSince I had already installed it once before, I received a message saying it was already registered.
Next, I pulled down Olaf Hartong’s modular Sysmon configuration:
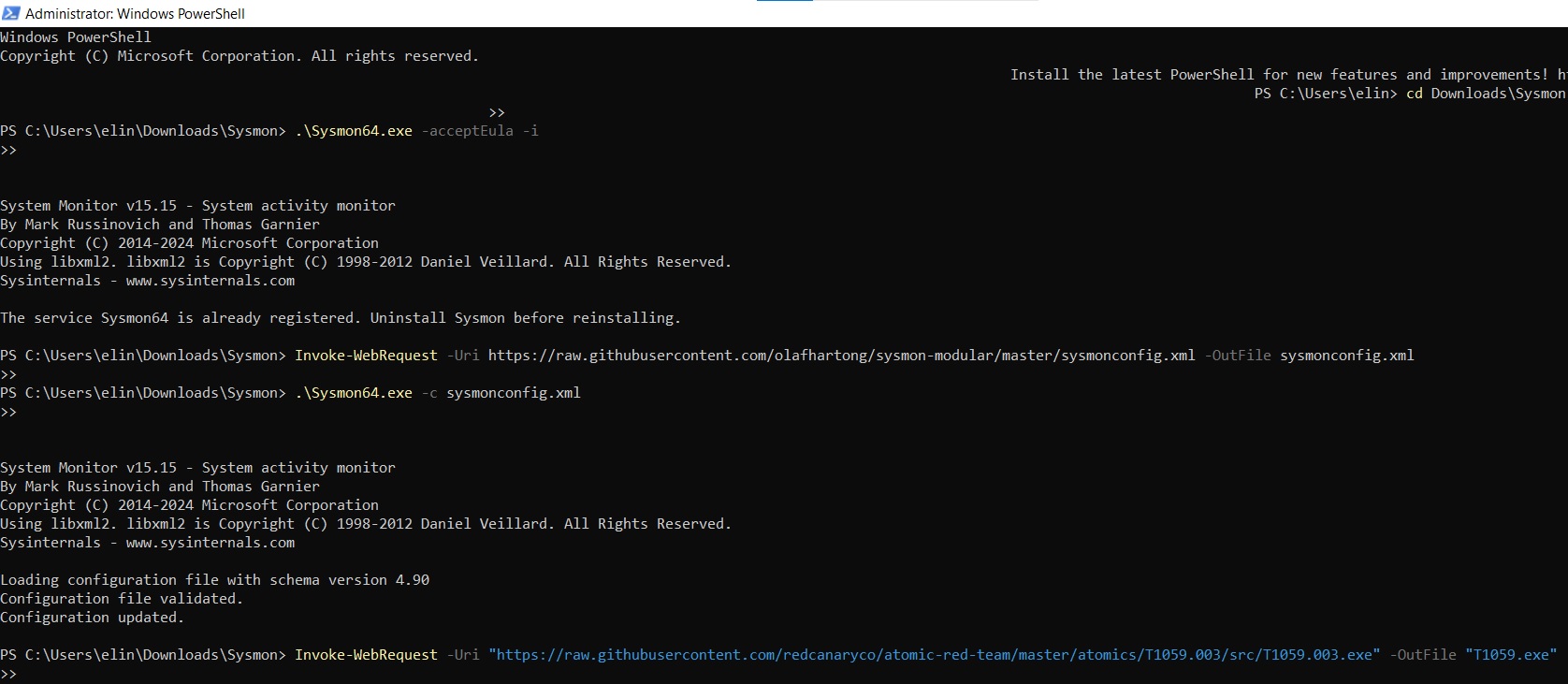
This loaded successfully and the configuration was validated.
Testing and Simulating Network Activity
After the configuration, I wanted to simulate network traffic. I download a few tools and extracted PsPing from Sysinternals.
I launched PsPing with:
.\psping.exe 127.0.0.1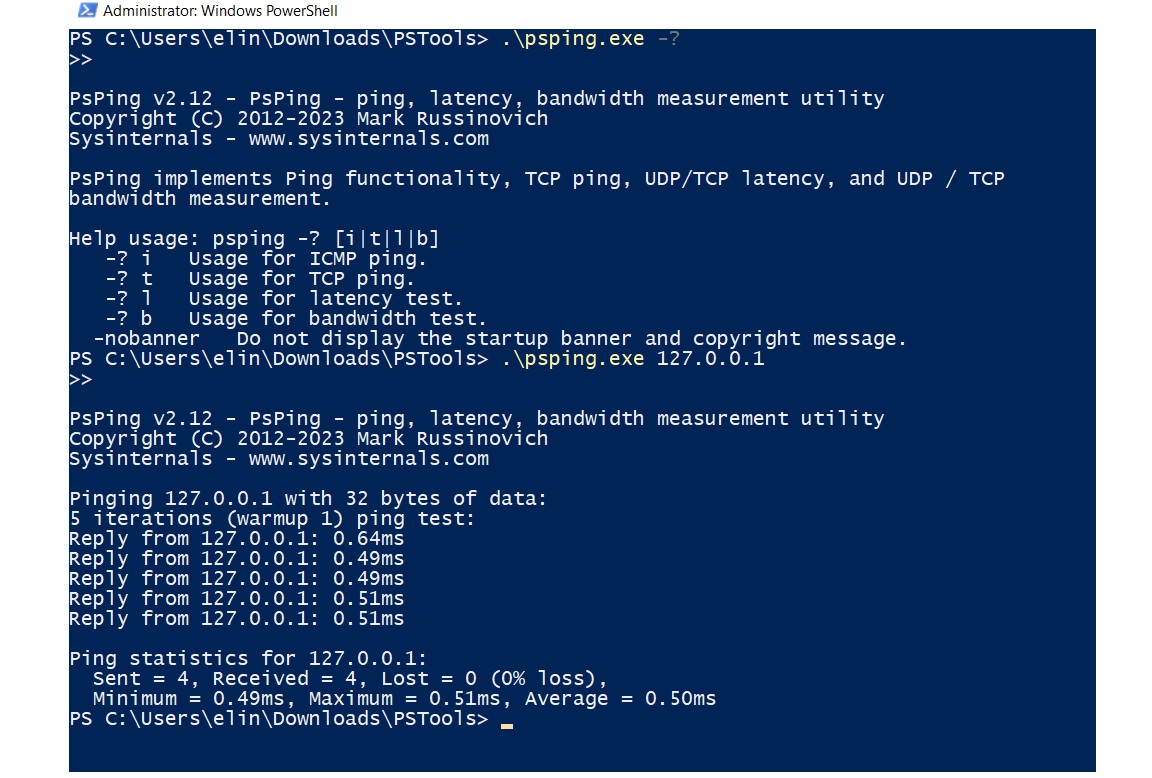
This generated network activity on the host, which we later observed in the Sysmon logs.
Log Analysis with Event Viewer
I opened Event Viewer and there, I filtered on Event ID 1 (Process Creation) and Event ID 3 (Network Connection Detected)
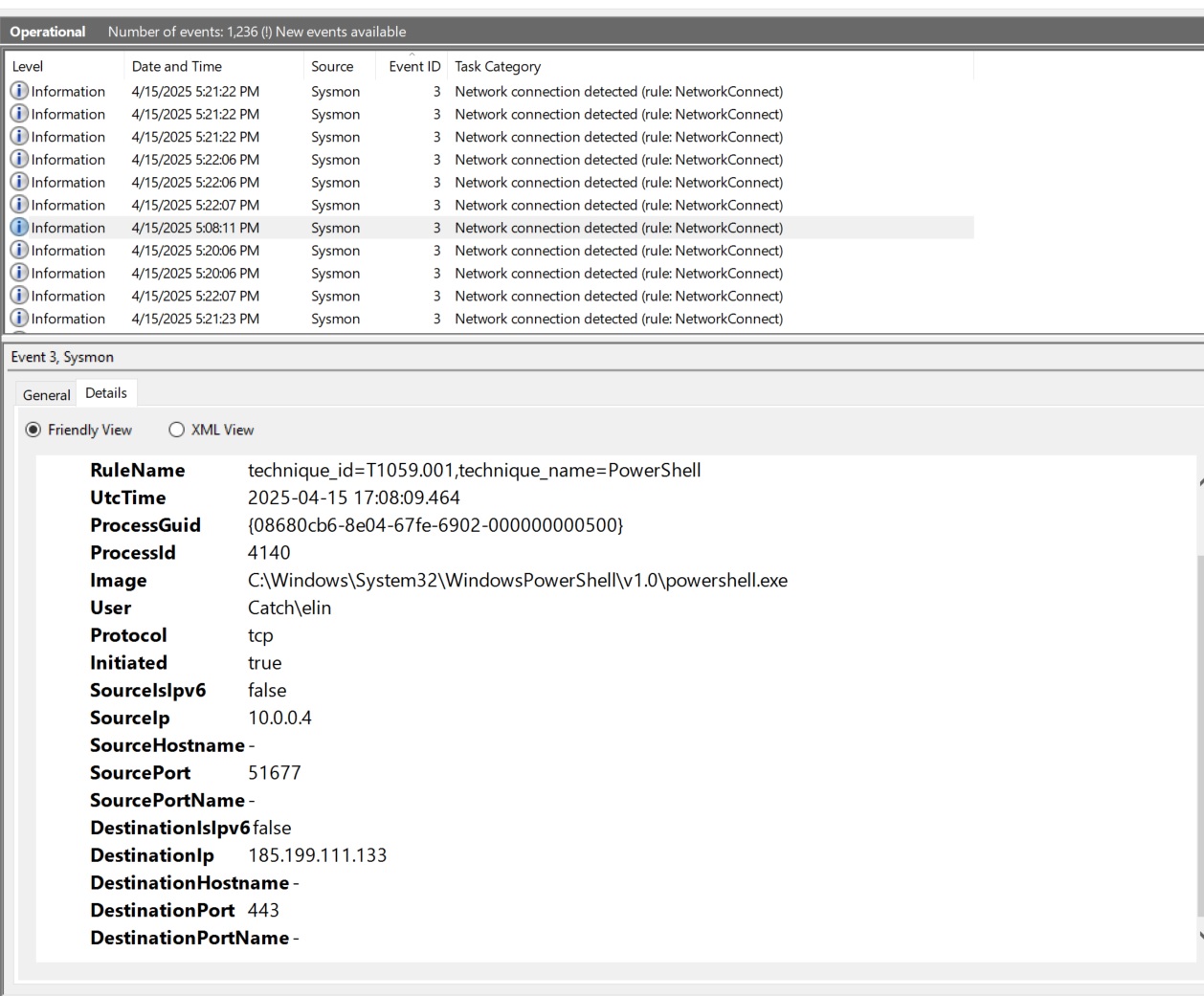
Here we see that PowerShell made an outbound TCP connection to IP 185.199.111.133 on port 443. This was the simulated T1059.001 (PowerShell) technique.
Example: Paint Execution (Event ID 1)
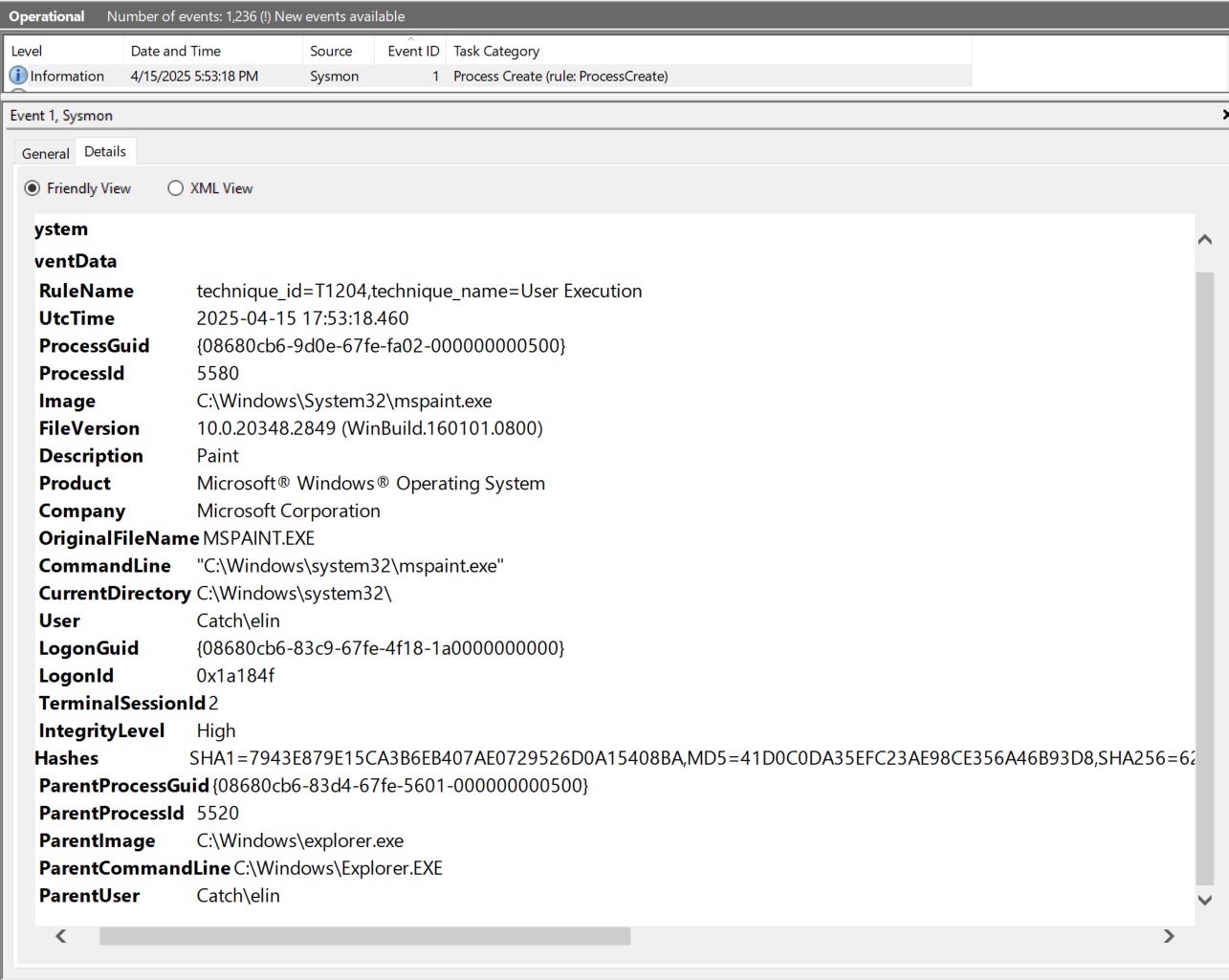
Even the opening of MS Paint is logged and tied to the correct user and parent process (explorer.exe). This proves our configuration is working and logging non-network activity too.
Detection Findings
| Event ID | Technique ID | Description | Comment |
|---|---|---|---|
| 1 | T1204 | User Execution (mspaint) | Normal user behavior |
| 3 | T1059.001 | PowerShell network call | Simulated threat |
| 3 | T1571 | Non-Standard Port (Edge) | Possibly benign browser traffic |
Lessons Learned
- Using a good Sysmon config is critical; Olaf Hartong’s rules are modular and effective.
- Not all network activity is malicious, but patterns (like PowerShell outbound connections) are strong.
- Logging and visualizing behavior makes investigation straightforward.
Stay tuned for Lab 2!

Lämna ett svar